
Tesla
Among the technologies that have spread more rapidly in recent years on cars that fall within a certain market segment, we find the one that allows you to access the car without the need to use the key, not even as a remote control; Tesla also uses it on its cars, although on more than one occasion it has been shown that it is an unsafe technology, easy to be circumvented by some attacker. The umpteenth example of this problem was brought by Sultan Qasin Khan, consultant for the English company specialized in cybersecurity NCC Group: speaking with Bloomberg, Khan shed light on the functioning of the BLE (Bluetooth Low Energy) data transmission protocol and on how this can be used by hackers to take control of the car's opening and ignition system.Unfortunately there is no real solution to this problem, or rather the There is a solution but it would be too expensive to implement: to make this system safer, the access system would have to be completely overhauled, also replacing the physical components on the car - and as we all know Tesla does not like to call his cars back to the workshop if it's not really strictly necessary.| ); }
As in the past, Tesla does not comment on these news, but the hope is that the company's IT team will always be working to make the keyless access system.
New Bluetooth hack can unlock your Tesla—and all kinds of other devices

Getty Images
When you use your phone to unlock a Tesla, the device and the car use Bluetooth signals to measure their proximity to each other. Move close to the car with the phone in hand, and the door automatically unlocks. Move away, and it locks. This proximity authentication works on the assumption that the key stored on the phone can only be transmitted when the locked device is within Bluetooth range.
Now, a researcher has devised a hack that allows him to unlock millions of Teslas—and countless other devices—even when the authenticating phone or key fob is hundreds of yards or miles away. The hack, which exploits weaknesses in the Bluetooth Low Energy standard adhered to by thousands of device makers, can be used to unlock doors, open and operate vehicles, and gain unauthorized access to a host of laptops and other security-sensitive devices.
“Hacking into a car from hundreds of miles away tangibly demonstrates how our connected world opens us up to threats from the other side of the country—and sometimes even the other side of the world,” Sultan Qasim Khan, a principal security consultant and researcher at security firm NCC Group, told Ars. “This research circumvents typical countermeasures against remote adversarial vehicle unlocking and changes the way we need to think about the security of Bluetooth Low Energy communications.”
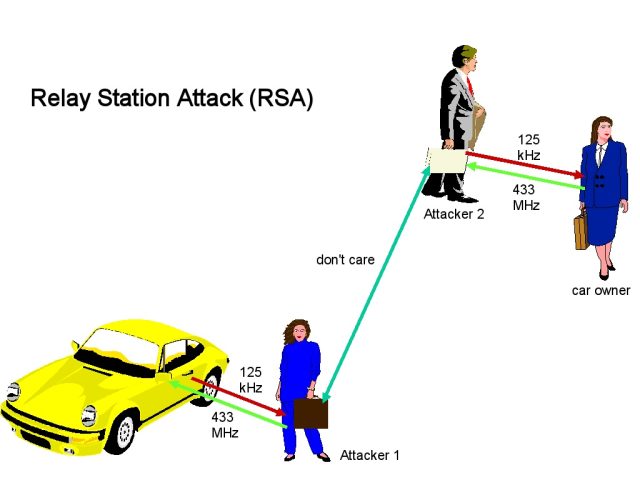
This class of hack is known as a relay attack, a close cousin of the person-in-the-middle attack. In its simplest form, a relay attack requires two attackers. In the case of the locked Tesla, the first attacker, which we’ll call Attacker 1, is in close proximity to the car while it’s out of range of the authenticating phone. Attacker 2, meanwhile, is in close proximity to the legitimate phone used to unlock the vehicle. Attacker 1 and Attacker 2 have an open Internet connection that allows them to exchange data.
AdvertisementAttacker 1 uses her own Bluetooth-enabled device to impersonate the authenticating phone and sends the Tesla a signal, prompting the Tesla to reply with an authentication request. Attacker 1 captures the request and sends it to Attacker 2, who in turn forwards the request to the authenticating phone. The phone responds with a credential, which Attacker 2 promptly captures and relays back to Attacker 1. Attacker 1 then sends the credential to the car.
With that, Attacker 1 has now unlocked the vehicle. Here’s a simplified attack diagram, taken from the above-linked Wikipedia article, followed by a video demonstration of Khan unlocking a Tesla and driving away with it, even though the authorized phone isn’t anywhere nearby.
Wikipedia
NCC Group demo Bluetooth Low Energy link layer relay attack on Tesla Model Y.
Relay attacks in the real world need not have two actual attackers. The relaying device can be stashed in a garden, coat room, or other out-of-the-way place at a home, restaurant, or office. When the target arrives at the destination and moves into Bluetooth range of the stashed device, it retrieves the secret credential and relays it to the device stationed near the car (operated by Attacker 1).
The susceptibility of BLE, short for Bluetooth Low Energy, to relay attacks is well known, so device makers have long relied on countermeasures to prevent the above scenario from occurring. One defense is to measure the flow of the requests and responses and reject authentications when the latency reaches a certain threshold, since relayed communications generally take longer to complete than legitimate ones. Another protection is encrypting the credential sent by the phone.
Khan’s BLE relay attack defeats these mitigations, making such hacks viable against a large base of devices and products previously assumed to be hardened against such attacks.